
HIPAA Compliance Solutions
Safeguarding Your Information Assets  xTerraLink awarded a contract with California Department of Public Health.
xTerraLink awarded a contract with California Department of Public Health.
 xTerraLink awarded an Independent Security Vulnerability Assessment the California Department of Tax and Fee Administration (CTDFA).
xTerraLink awarded an Independent Security Vulnerability Assessment the California Department of Tax and Fee Administration (CTDFA).
 xTerraLink awarded an Independent Security Assessment based on California AB670 for the California Department of Insurance (CDI).
xTerraLink awarded an Independent Security Assessment based on California AB670 for the California Department of Insurance (CDI).
 xTerraLink partnered with IBM to help support the CCPA compliance Privacy Program.
xTerraLink partnered with IBM to help support the CCPA compliance Privacy Program.
 xTerraLink recently selected and awarded a contract with California Department of General Services.
xTerraLink recently selected and awarded a contract with California Department of General Services.
xTerraLink was awarded a California State Board of Equalization enterprise wide independent security architecture assessment contract. xTerraLink's unique Information Security and Privacy Assessment Framework coupled with its experience edged xTerraLink over its closest competitor.
 xTerraLink's President was part of a subject matter expert panel on information security.
xTerraLink's President was part of a subject matter expert panel on information security.
 xTerraLink was awarded a contract with the California State Auditor.
xTerraLink was awarded a contract with the California State Auditor.
 xTerraLink was awarded a subcontract agreement with the State Compensation Fund to help support the Fund's Information Security Program.
xTerraLink was awarded a subcontract agreement with the State Compensation Fund to help support the Fund's Information Security Program.
Access Workflow Automations

An access control limits the use of a resource. Only those people, programs or devices that are specifically permitted to use the resource will have access. In addition, an access control will usually limit use to specific types of access; someone can read a file but not change it, for example. An access control may be physical, for example, a lock on a door; or it may be software or hardware based, for example, in a computer system. It can also be a combination of the two. In an organization, access management is the sum of all of the practices, policies, procedures, and technical access control mechanisms that are used to appropriately control access to the assets, or a subset of the assets, of the company. Controlling access is managed through a well-integrated access workflow management process.
Forensics and Data Recovery

For most organizations, it is a matter of when, not if, they will need to comply with a request for electronically stored information (ESI) from a government agency or opposing party in a lawsuit. Is your enterprise ready?
HIPAA Privacy and Security Compliance
xTerraLink provides a HIPAA Privacy and Security Compliance Program for independent small and medium Dental, Medical, Therapists or any practices that provide and manage patient care. xTerraLink's HIPAA Compliance Framework includes the following:
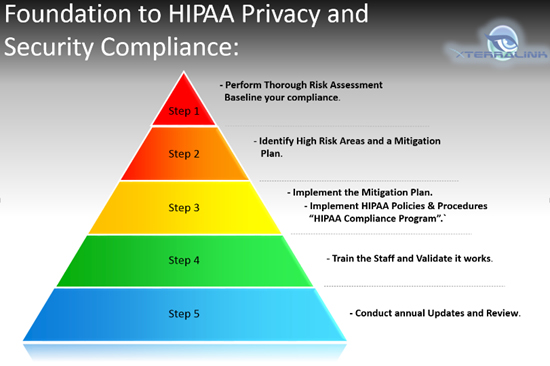
When your Practice implements xTerraLink's HIPAA Compliance Program components and stays aligned with the program by conducting regular reviews, your HIPAA compliance becomes easily maintainable.
Learn More about Pricing Plans
Incident Tracking and Reporting
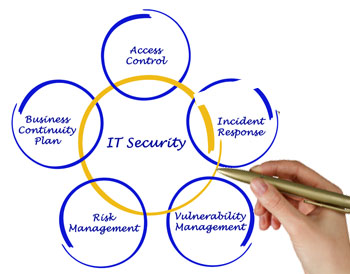
Computer security incident management involves the monitoring and detection of security events on a computer or computer network, and the execution of proper responses to those events. Computer security incident management is a specialized form of incident management, the primary purpose of which is the development of a well understood and predictable response to damaging events and computer intrusions. Does your organization have the right incident management program?
Information Asset Auditing and Reporting

Information management (IM) is the collection and management of information from one or more sources. Management means the organization of and control over the structure, processing and delivery of information which results in compliance.
Penetration Testing
Security Penetration Testing is a method of evaluating the security of a computer system or network by simulating an attack from malicious outsiders (who do not have an authorized means of accessing the organization's systems) and malicious insiders (who have some level of authorized access). The process involves an active analysis of the system for any potential vulnerabilities that could result from poor or improper system configuration, both known and unknown hardware or software flaws, and operational weaknesses in process or technical countermeasures. We carry this from the position of a potential attacker and can involve active exploitation of security vulnerabilities to help your organization mitigate those vulnerabilities before they are exploited by a real intruder/attacker.
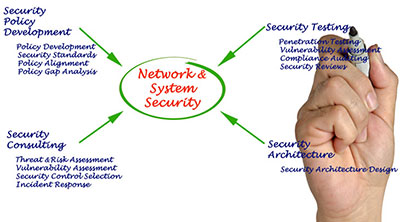
Risk Management

Protecting information and information systems from unauthorized access, use, disclosure, disruption, modification, perusal, inspection, recording or destruction are the common goals for confidentiality, integrity and availability of information. As such, risk management is the process of implementing and maintaining appropriate management controls including policies, procedures and practices to reduce the effects of risk to an acceptable level. The principles of risk management can be directed to both limiting adverse outcomes and achieving desirable ones. The process involves identifying, analyzing, assessing, treating and monitoring risk in all areas of an organization's operations and business. Our team brings methodologies to help your organization identify and prioritize risks as they pertain to various regulatory compliance components.
Simple All-In-One HIPAA Package Solution Pricing
Pilot Package (Limited Time Offer)
- Customized Dashboard with Site Management & Settings
- Unlimited Number of Users
- Custom Generated Policies & Procedures
- Unlimited Use of ALL State Specific HIPAA Privacy and Security Forms and Reports
- Unlimited HIPAA Risk Assessments & Reports with Revolving Ongoing Maintenance
- Unlimited Use of the Automated HIPAA IT Security Compliance Module Scanning and Reports
- Unlimited On-Demand HIPAA Security Training & Employee Training and Credit Tracking
- Unlimited Use of Business Associate Agreements
- Customized Business Continuity Plans
- State Specific Incident Response Plan
- Risk Assessment, On-Going Maintenance, IT Risk Analysis Reports Review: No Charge
- Security & Privacy Reminders: No Charge
- Security and Privacy Video and Messaging and Reminders: No Charge
- Secure Embedded Email Correspondence with xTerraLink: No Charge
- On Demand Program Progress Reviews: No Charge
- Access to Customer Service, LiveChat & Unlimited Updates: No Charge

